The internet has become the mainstay of almost every modern business. Every other discrete system connects over the internet for its transactions, be it economic or non-economic. This is when businesses become sceptical about their personal or confidential information. Systems and information are becoming more vulnerable to smart hackers, and a constant vigilance is a necessity to protect systems and information against these new threats. Any lapse in security policies will be at the cost of your credibility and revenue. The key to secure your network involves laying out strict guidelines on physical and virtual access, authentication, administration and monitoring.


Why We
Exponential growth of IP networks over the past few years has raised the threats to information, primarily unauthorized access to resources and sabotage. We at iNetSpine help you adhere to regulatory requirements and protect your machine’s critical systems and information. With solid security acumen, discovering potential vulnerabilities and its business impacts comes handy in selecting the right security routines.
What we do.
Enterprise security designing
Knowing your threats is the key to building an effective security design. Reinforced by our expertise in enterprise security and extensive understanding of the current real world scenarios, we help you to manage the next generation threats. We perceive security as business enablers, and this holistic approach to security safeguards your information. Our robust security designs provide a flawless equilibrium among people, technology and processes.
Enterprise unified threat management solution
Be fully prepared to safeguard your enterprise against future threats that may originate internally or externally within your organization. With our next generation unified security management solutions, we help you simplify operation, innovate faster and reduce risks. By placing emphasis on your environment and security needs, we offer the right security controls, thus ensuring strong governance for your processes. Among the other main solutions offered by unified security management are gateway antivirus, VPN, content filtering and firewall that can prevent network intrusions.
Vulnerability Assessment
Each organization has its own security challenges and a thorough understanding of the assessment process will assist in taking preemptive measure against vulnerabilities. From security survey to internal process audits, we help you identify potential weaknesses in your infrastructure and applications. Our outcome based security questionnaires are no more a waste of time for your employees and service providers, but rather serves as a means of improving the productivity.
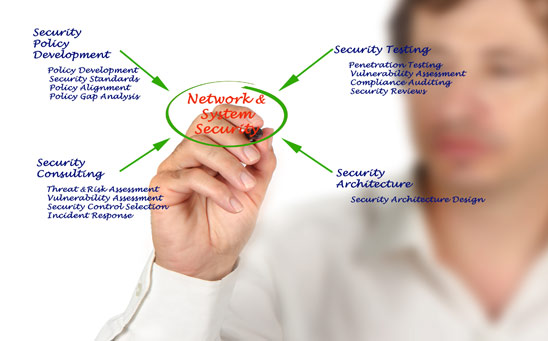
Enterprise security assessment & Improvements
Security management is not a one-time initiative; rather it is a continuous process requiring time and resources. Improvements in security policies are essential in the ever-shifting business and technological environment. Be it being on the lead with the advanced security process or incident management in compliance with evolving standards, our consultants provide guidance on strategic security decision.
IT Infrastructure
The ever-increasing nature of competition in business world prompts IT enterprises to become dependent on infrastructure that can cope with the changing trends in the market.
Hardware as a Service
We have been the first choice of company for many businesses when it comes to equipment rental of IT hardware.
Network Solutions
An enterprise network is the mainstay of communication for any organization and the inability of networks to adapt to advancements in technology and traffic often leads to business failure.
Mobility Solutions
Mobility at workplace is evolving largely through a plethora of wireless devices.
Servers and Virtualization solutions
Discover the power of virtualization by inventive consolidation of your data center and mission critical application servers.

